CORE’s Bug Bounty Program

We call on our community and all bug bounty hunters to help identify bugs in our ecosystem. CORE recognizes the importance and value of security researchers’ efforts in helping keep our community safe. Our Bug Bounty Program rewards members of the community for helping us find and address significant bugs. Earn rewards for finding a vulnerability and get recognized on our leaderboard.
Rules:
Responsible investigation and reporting include, but is not limited to, the following:
Do not violate the privacy of other users, destroy data, or disrupt our services
Do not target our physical security measures, or attempt to use social engineering, spam, distributed denial of service (DDOS) attacks, etc.
Initially report the bug only to us and not to anyone else.
Public disclosure of a vulnerability would make it ineligible for a reward
Provide us a reasonable amount of time to fix a vulnerability prior to sharing details of the vulnerability with any other party
Rewards will be decided on a case by case basis at the sole discretion of the CORE team.
Issues that have already been submitted by another user or are already known to the CORE team are not eligible for bounty rewards
Bounty Scope
The CORE Bug Bounty Program covers security issues identified in the following repository:
Vulnerabilities Classification
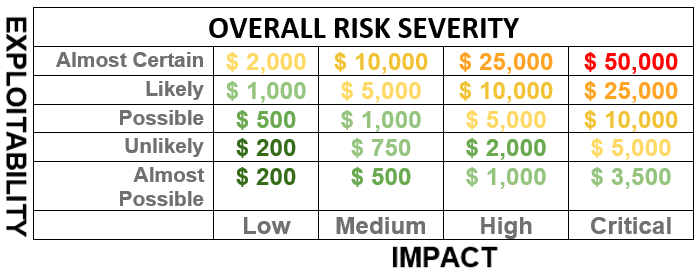
CORE awards bounties based on severity of the vulnerability. The severity is determined by the impact and exploitability of a bug.
Impact describes the extend of a successful exploitation on CORE’s ecosystem. Exploitability describes the difficulty to perform the vulnerability. The Severity is a combination of the Impact & Exploitability. We use the Severity of a report to place the report into the appropriate tier.
Decisions on the eligibility and size of the reward are guided by the points below, but are, in the end, determined at the sole discretion of the CORE team.
SEVERITY TIER:
Critical: up to $50,000
High: up to $25,000
Medium: up to $10,000
Low: up to $2,000
Every bounty is allocated points which accumulate over the course of the program. Based on total points, participants may be recognized in our Leaderboard.
Other considerations:
In addition to our Severity tier, we consider also other variables when evaluating the eligibility and size of a bounty.
Quality of Description: well-written and clearly structured reports receive higher rewards
Reproducibility: Please describe your claim in as much details as possible. The easier it is for us to reproduce and verify the claim, the higher the reward
Suggestion of Fix: We pay higher rewards to submissions with clear description of how to fix the issue.
Submission process:
Responsible disclosure can be made by emailing [email protected]
Try to include as many details as possible about the vulnerability, potential impact, steps for reproducing it as well as possible fixes
Please allow 2 days for us to respond before sending another email.
Last updated